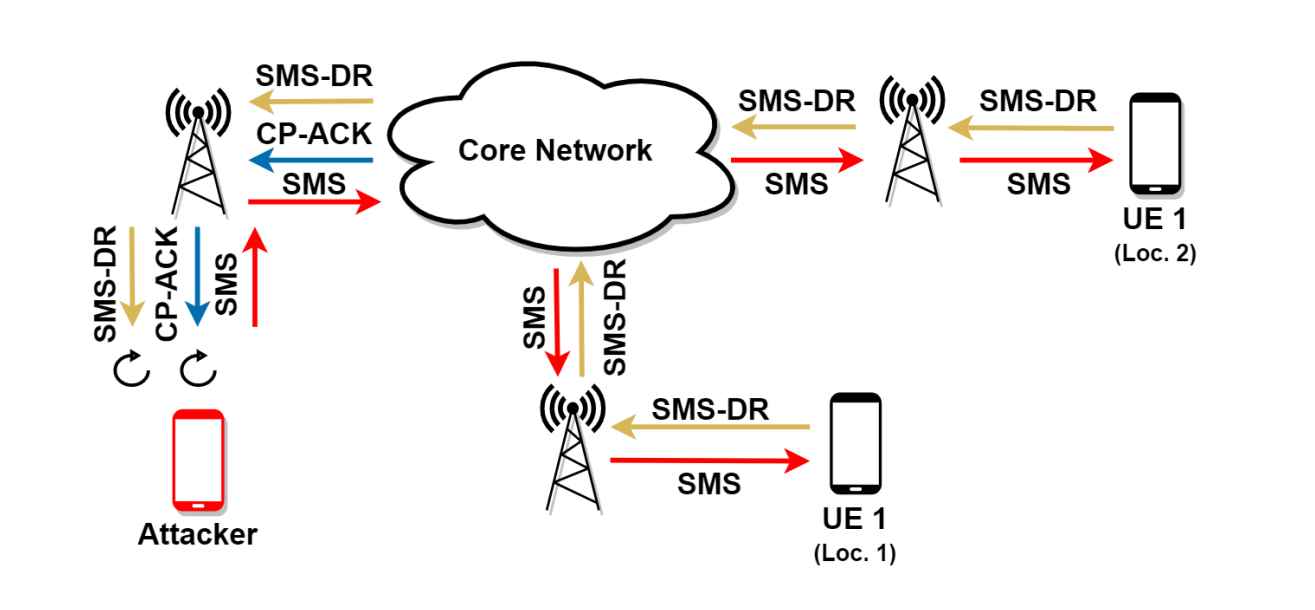
SMS delivery reports not only inform the sender that the message was successfully delivered, but they also have the potential to provide the location of the receiver. This is what the researchers have proved in their most recent work, which shows how receiving a silent SMS message activates a side-channel attack, allowing the sender to estimate the position of the receiver based on the timing of the messages received by the recipient. Researchers from a variety of colleges collaborated on the development of an innovative side-channel attack that reveals users’ whereabouts through SMS. Taking advantage of the SMS delivery reports seems to be the technique of attack, according to the information that was presented in their study paper. A sender may estimate the location of the receiver across several nations with an accuracy of up to 96% using the statistics that were acquired from the timings of these message exchanges. Exploiting the GSMA network’s core vulnerabilities, which are what drives the technology behind SMS messages, is the primary focus of this attack.
This side-channel attack affects almost all cellular networks across the world since it generally targets GSMA. Despite the availability of other communication options, such as 3G and 4G, the researchers were interested in studying SMS because of its prevalence as a way of 2G communication among the general public. The researchers made the observation that the SMS Delivery Reports that are inevitably created after receiving an SMS message cause a timing-attack vector to be triggered. Knowing the timings of message delivery and estimating the time gap between message sending and receiving might assist a sender establish the location of the receiver if the sender has enabled SMS Delivery Reports. since of the way the SMS Delivery Reports feature operates, the user of the recipient cannot prohibit harmful use of this tool since it is outside of the recipient’s control. The approach, in its most basic form, makes use of the temporal signatures associated with a particular site.
The more exact the data that the attacker has on the whereabouts of their targets, the more accurate the location classification results that the ML model will provide for its predictions when it comes to the attack phase.
The data can only be obtained by the attacker sending several SMS messages to the target, either by disguising them as marketing communications that the target would ignore or discard as spam or by utilizing quiet SMS messages. A silent SMS is a “type 0” message that has no content and does not create any alerts on the screen of the target device; nonetheless, its receipt is still confirmed by the device on the SMSC. The authors of the research conducted their studies by using ADB to send bursts of 20 silent SMSes every hour for three days to several test devices located in the United States, the United Arab Emirates, and seven European nations. This experiment covered ten different operators and a wide range of communication technologies and generational differences.
By sending SMS messages to the target user at a variety of different times and places, an adversary may acquire numerous timing signatures associated with the person. The sender may be able to determine the location of the recipient by analyzing them at a later time. To carry out this attack, the adversary need only be in possession of the cell phone number of the victim they are targeting. Even though it is a time-consuming process, collecting and analyzing the timing signatures of the target user might provide an adversary the ability to discover a previously unknown or new location of the individual they are targeting. This operates correctly regardless of the user’s location, whether it in the United States or elsewhere in the world. The amount of time that passes between when an SMS is sent and when it is received might be helpful here.
Even while the researchers were able to reach a high level of precision when carrying out their side-channel attack, it does have a few drawbacks. This is due to the fact that there are a variety of variables that might influence the empirical measurements in a real-world exploit. Even in a hypothetical situation in which the globe is locked off, the still-unachievable accuracy of more than 90 percent presents a risk to individuals’ privacy. In terms of the countermeasures, the researchers noted that the current ones to avoid similar attacks do not apply to this unique side-channel attack. This is because the novel attack uses a side-channel that does not present in the related attacks. Not delivering Delivery Reports or altering them with a random delay are also potential tactics that might be used in the fight against delays in UE processing. As for the delays that are caused by the network itself, modifying the SMS timings, installing spamming filters on the core network, or at the very least turning off quiet messages will help reduce the likelihood of an attack of this kind happening. Nevertheless, turning off the component that generates delivery reports may be the only practical preventative action. Before making this study available to the general public, the researchers acted appropriately and informed the GSMA about the situation. In response, the GSMA accepted their results (which were given the identifier CVD-2023-0072) and evaluated a variety of preventative actions.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
How to hack & track anybody's phone location via silent SMS … – Information Security Newspaper