In late June 2025, Sekoia.io’s Threat Detection & Research (TDR) team observed anomalous POST requests to Milesight Industrial Cellular Routers, which triggered the mass distribution of phishing SMS messages.
By exploiting an unauthenticated API endpoint at /cgi, attackers dispatched JSON-formatted payloads that invoked SMS delivery functions. Initial traces were recorded on 22 July 2025, all linked to IP address 212.162.155.38 within AS Podaon SIA.
Sekoia.io deployed honeypots emulating Milesight UR5X and UR32L routers to monitor edge-device traffic.
Honeypot logs revealed repeated POST requests carrying parameters such as function: "send_sms" base: “api_sms”, alongside JSON values specifying recipient numbers and message content.
Unauthenticated calls to query_outbox and query_inbox exposed SMS histories, including transmission timestamps, message texts, international phone formats, and delivery statuses.
Numerous “failed” statuses to the exact controlled numbers suggest a validation step: attackers first verify each router’s SMS capability before launching full-scale campaigns. This approach reduces wasted effort on non-functional devices and serves as an indicator for clustering attack campaigns.
A comprehensive Shodan census identified over 19,000 Milesight routers publicly reachable on the internet. Sekoia.io tested a subset of 6,643 IPs, discovering 572 routers with unauthenticated access to their SMS APIs.
Firmware versions 32.2.x.x and 32.3.x.x accounted for the majority of vulnerable devices, though two routers on firmware 41.0.0.2 and 41.0.0.3 were also exposed.
Geographic distribution skews heavily toward Europe, with France, Belgium, and Turkey hosting the highest concentrations of at-risk devices. Smishing sample analysis dates back to February 2022, indicating an enduring campaign.
Two primary SMS distribution patterns emerge: simultaneous mass blasts and repeated, targeted subset campaigns.
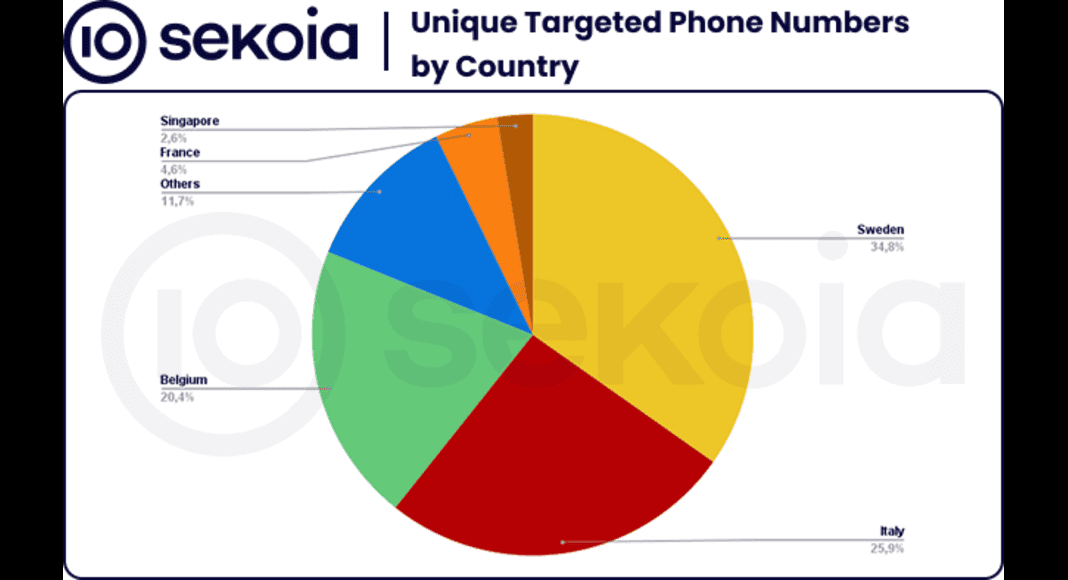
For instance, in May 2025, attackers transmitted identical messages to 42,044 Swedish numbers and 31,353 Italian numbers via domains like estrk.xyz/SE and jnsi.xyz/IT, exemplifying mass-drip strategies.
Belgian recipients experienced the most persistent targeting, with campaigns impersonating CSAM and eBox the nation’s federal authentication portal and centralized digital mailbox.
Typosquatted domains such as csam.ebox-login.xyz and ebox.csam-trust.xyz delivered Dutch- and French-language lures urging users to view “important messages” or process “annual tax returns” using weaponized shortened URLs.
French victims encountered a wider range of impersonations, spanning health insurance (assurancemaladie-renouvellement.info), postal services (logistique-infosms-laposte.fr), and banking (service-interbancaire.page.dev).
All phishing pages enforce mobile-only access via JavaScript ontouchstart checks, returning HTTP 500 errors for desktop clients. Obfuscated scripts detect_device.js and maghat_lebssouch.js—Disable right-click and debugger functions, hindering forensic analysis.
Domain registration data points to NameSilo and hosting on Podaon SIA VPS servers. Phishing infrastructure pivots include GitHub-hosted “GroozaV2” assets and a Telegram bot “GroozaBot” for real-time visitor logging.
Linguistic artifacts in JavaScript logs and Telegram chat snippets reveal the actor operates in Arabic and French and has connections to Thailand.
The use of multiple autonomous systems in Lithuania (AS210895) and Russia (AS211860) for distinct clusters underscores operational sophistication and redundancy. This modular, mobile-gated architecture enables region-specific lures and rapid domain turnover.
The exploitation of SMS-capable routers for smishing campaigns underscores the urgency of securing IoT and edge devices. Organizations should perform the following actions:
Heightened vigilance, combined with proactive patch management and infrastructure monitoring, is crucial to disrupt smishing operations that exploit misconfigured routers to scale SMS weaponization.
CSAM/Ebox – Domains
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
Exclusive Cyber Security News platform that provide in-depth analysis about Cyber Attacks, Malware infection, Data breaches, Vulnerabilities, New researches & other Cyber stories.
Contact Us: [email protected]
© Copyright 2024 – Cyber Press
Threat Actors Use Cellular Router API to Flood Phones with Weaponized Links – Cyber Press