 Smishing is phishing via Short Message Service (SMS) on a participating device, usually a cell phone. Long neglected by phishers and spammers, smishing has recently become a very common way of spamming, phishing, and spear phishing potential victims. KnowBe4 has been covering and warning users about it and its coming rise for years.This blog post will cover why smishing is becoming so popular, show some general and more sophisticated examples, and discuss defenses.
Smishing is phishing via Short Message Service (SMS) on a participating device, usually a cell phone. Long neglected by phishers and spammers, smishing has recently become a very common way of spamming, phishing, and spear phishing potential victims. KnowBe4 has been covering and warning users about it and its coming rise for years.This blog post will cover why smishing is becoming so popular, show some general and more sophisticated examples, and discuss defenses.
Short Messaging Service (SMS) is a popular text-based messaging service standard, which nearly all cell phones support. Already in widespread use by the 1990s, it is rare that a cell phone doesn’t support SMS, which originally only allowed a maximum of 140- to 160-characters to be sent in a single message to one or more other recipients using their cell phone numbers. The original message size limitation was due SMS’ reliance on an underlying phone protocol known as Signaling System No. 7 (SS7). Today, depending on the mobile network vendor and involved applications, SMS-based apps can send longer messages and more than simple text-based characters (such as emoticons, pictures, videos, etc.).
The biggest problem from a security perspective is that an SMS sender is not authenticated beyond attached phone numbers. Anyone receiving an SMS can only, at best, be assured at the phone number the SMS message comes from is accurate, and even that isn’t guaranteed. There are many rogue applications which allow senders to send SMS messages from spoofed or borrowed/shared telephone numbers.
SMS is unauthenticated, meaning anyone can send another person an SMS message by simply knowing the recipient’s phone number. And as long as that person hasn’t previously noted the number as a particular sender’s ID and stored it in their contact list, it will show up looking like any other SMS message without an authenticated name attached. I, and anyone else, can be anyone via SMS. A receiver might not believe the sender is the President of the United States (unless they already have a formal relationship with the President), but otherwise most people are susceptible to simply accepting that the SMS sender is who they claim to be.
Additionally, URL (Uniform Resource Locator) links sent via SMS are often harder to inspect for security issues without completely loading the web page the link points to. SMS URL links are often “shortened” to some innocuous-looking link that is hard to figure out where it ultimately links to. So, a URL link might say something like https://bit.ly/Y7acoe and when open, might redirect to something that looks like https://thisisabadwebsite.com/virus.php. Most smishing includes shortened URLs which are intended to hide the eventual destination.
Security people aren’t big fans of URL shortening services in general, but when paired with limited pre-inspection capabilities of SMS and lack of authentication, there are even more reasons to be skeptical. Users cannot “hover” over an SMS URL to find out where it ultimately goes to, and SMS applications don’t contain nearly as many anti-malicious controls as the typical browser does (although many times, SMS URLs are opened up in the user’s browser anyway). All-in-all, as our online world is increasingly becoming one conducted by cell phone, smishing is growing in popularity with attackers.
Here are some general real-world smishing examples I’ve received on my personal cell phone recently.
This one is attempting to appear as if it’s from the U.S. Internal Revenue Service (IRS).
I get a lot of these, where they appear to be responding to an order I have supposedly created. Most people, who have not recently created an order, would be curious about what company is supposedly claiming they have placed an order and be worried about whether they will somehow be charged or not.
This sender of fake SMS order messages appears to resend from the same fake originating phone number, but claims to be different senders with different URLs.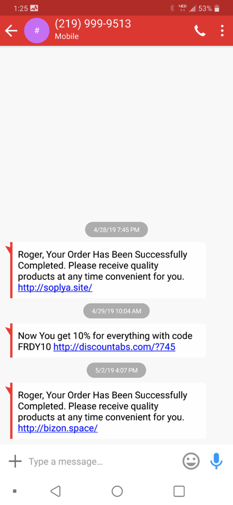
This fake SMS message might appear more realistic because it is using Google’s own URL shortening service (goo.gl).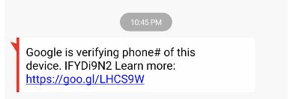
This one claims I’m a winner of a Walmart gift card, although they apparently have me mixed up with someone called Timoth.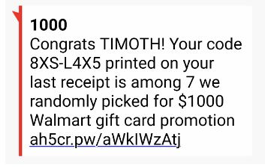
This one almost tricked me. I travel for a living and I stay in a lot of different hotels. When I got this one, I just checked out of a new hotel. It was a fake SMS message though. The URL link led to a rogue pharmacy site where I could buy all the erectile dysfunction pills I wanted.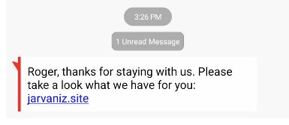
The following message was sent to multiple people in my previous company.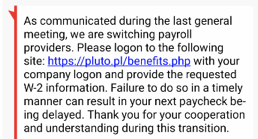
Now, those previous fake SMS messages seem more like run-of-the-mill spam, although some tried to install malware on my phone. These next few examples show greater harm that can be done by using fake SMS messages.
Here’s how the attack goes:
This is a very common type of phishing scam, although the scammer may claim to be from your bank, investment company, PayPal, airline, hotel company, or any other entity you have a membership and financial information with. In all cases, they will claim to have detected some sort of rogue activity or attempt, and claim to be saving you from the criminal activity. They will then claim to be sending you a code via SMS that you need to tell them to verify that “you are who you say you are”, and when you tell them that code (sent by your service’s legitimate automated recovery service), they take over your account. This type of scam is done thousands of times a day and can fool even the most skeptical among us.
This one I blame on my own carelessness. I was upset about a fairly new refrigerator that I owned, which broke down three times in the first two years. I contacted the vendor’s Facebook site and posted my rant against their product claiming I wasn’t happy with my “lemon”, even though it was under warranty. Apparently, phishers lurk on public vendor support sites waiting for people like me to complain publicly. I immediately received a Facebook private message from a fake vendor support person claiming they were going to help me as well as a related fake SMS message the next day. I’m still not sure how they got my telephone number to send the SMS message, but I used to include my phone number in every email I sent for decades, so it probably wasn’t too hard to find.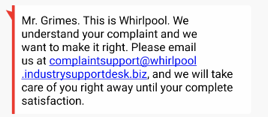
Although smishing is harder to defend against than regular email phishing attempts, there are defenses that can reduce the risk of successful attacks.
Overall, you want to create a culture of security awareness training and healthy level of skepticism around SMS messaging. Smishers are increasingly using SMS to conduct phishing and spear phishing attacks. Get ahead of the increasing problem by fighting and defending against smishing today. If you have any questions about smishing or defenses, please don’t hesitate to contact us!
Return To KnowBe4 Security Blog
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget. Here’s how it works:
Here’s how it works:
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-security-test-offer
Topics: Social Engineering, Phishing, Security Awareness Training
Roger A. Grimes, Data-Driven Defense Evangelist for KnowBe4, Inc., is the author of 15 books and over 1500 articles, specializing in host security and preventing hacker and malware attacks. Roger is a frequent speaker at national computer security conferences and his presentations are fast-paced and filled with useful facts and recommendations.
Security Awareness Training
Blog RSS Feed
SMS Phishing (Smishing) Examples & Defenses | KnowBe4 – KnowBe4 blog

