A new Android malware campaign uncovered by Cyble Research and Intelligence Labs (CRIL) is exploiting the guise of India’s Regional Transport Office (RTO) applications to steal banking data and UPI credentials.
Identified as “GhostBat RAT,” the malware employs advanced obfuscation, multi-stage droppers, and social engineering to target Indian users through fake mParivahan apps distributed via WhatsApp, SMS, and compromised websites.
The GhostBat RAT campaign leverages deceptive links shared via WhatsApp and SMS messages, which contain shortened URLs leading to GitHub-hosted APKs or malicious websites mimicking official government platforms.
Once installed, the fake mParivahan app requests SMS permissions under the pretext of an app update and immediately begins harvesting sensitive data.
CRIL analysts identified over 40 malicious APK samples since September 2025, most featuring multi-layered evasion techniques such as ZIP header manipulation, custom packers, and anti-emulation mechanisms.
The malware’s initial dropper decrypts embedded payloads using XOR and AES algorithms, with each subsequent stage deploying additional components including an infostealer and a cryptominer.
Native libraries (.so files) are used to dynamically resolve API calls at runtime, adding another layer of complexity to reverse engineering efforts.
The primary dropper verifies the device’s architecture to avoid analysis environments and then decrypts and executes secondary payloads using DexClassLoader.
Subsequent stages assemble and execute native libraries to deliver the final malicious APK responsible for phishing and data exfiltration activities.
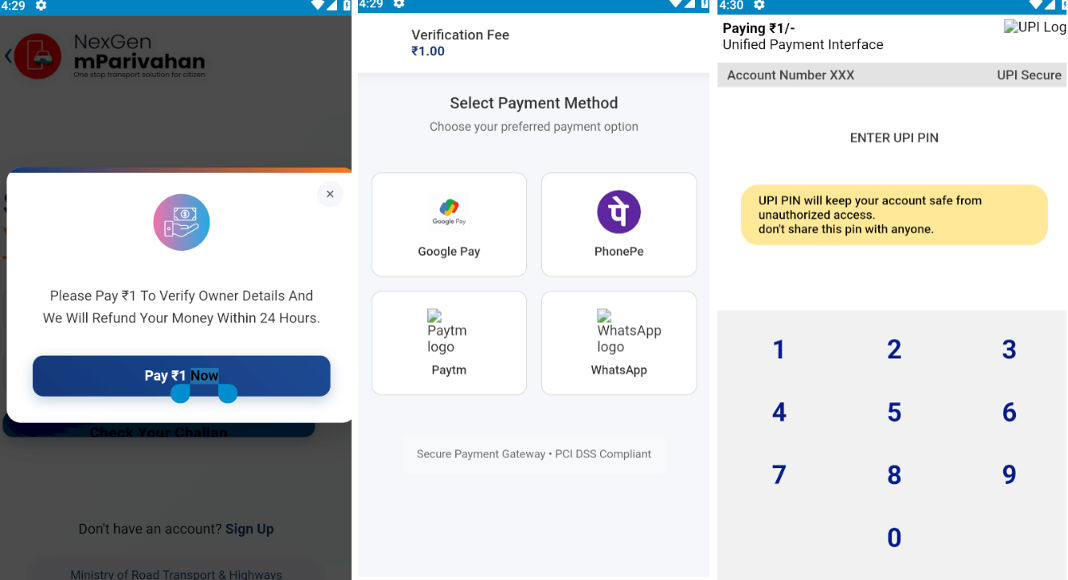
Once the malicious mParivahan clone is installed, users encounter a fake “Google Play update” prompt, leading to the installation of the malware payload.
The app then launches a phishing page requesting users’ mobile numbers and vehicle details, eventually initiating a ₹1 “verification” payment.
This flow presents a counterfeit UPI interface where victims are tricked into entering their UPI PINs, which are subsequently sent to a Firebase endpoint controlled by the attackers.
The malware also exfiltrates SMS messages containing banking-related keywords and monitors incoming OTPs. Notably, all infected devices are registered automatically via a Telegram bot named “GhostBatRat_bot,” establishing real-time C2 communication and linking the entire campaign to the GhostBat RAT operation.
According to CRIL, the malware represents a significant advancement in RTO-themed Android attacks, combining cryptomining with credential theft and advanced detection evasion.
Users are advised to install apps only from trusted sources, enable multi-factor authentication, and use reputable mobile security software to prevent infection.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
Exclusive Cyber Security News platform that provide in-depth analysis about Cyber Attacks, Malware infection, Data breaches, Vulnerabilities, New researches & other Cyber stories.
Contact Us: [email protected]
© Copyright 2024 – Cyber Press
GhostBat RAT Masquerades as RTO Apps to Loot Banking Data of Indian Android Users – Cyber Press