Security researchers at Zimperium’s zLabs have discovered a new and far more dangerous variant of ClayRat, an Android spyware campaign that continues to evolve rapidly.
First detected in October, ClayRat was initially known for stealing SMS messages, call logs, photos, and notifications.
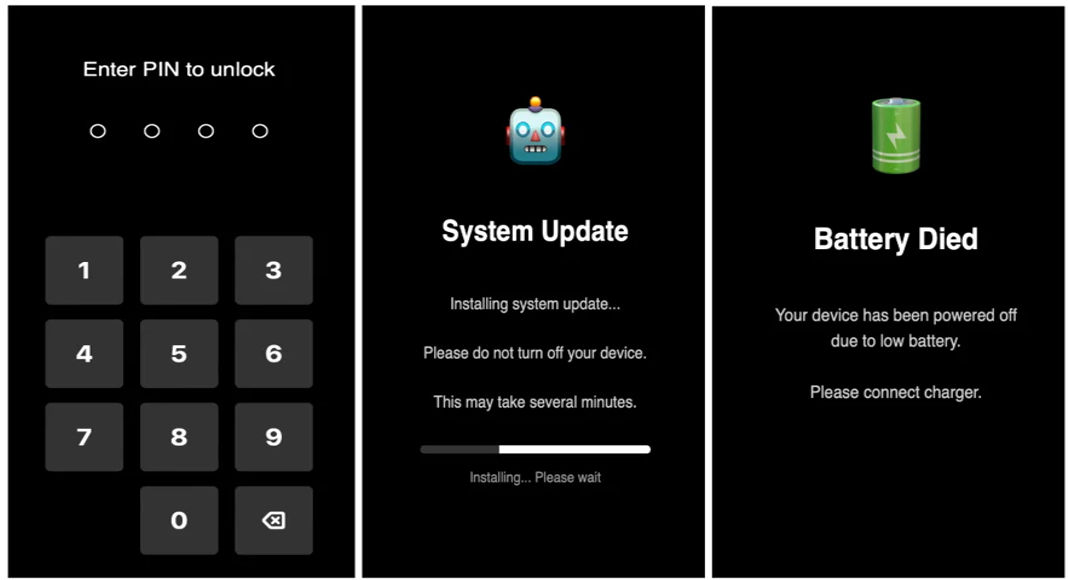
The latest version, however, takes control of an infected device through Accessibility Services abuse, enabling keylogging, screen recording, phone locking and unlocking, and even impersonating notifications.
In its updated form, ClayRat now employs Accessibility Services alongside default SMS handler privileges to gain deep system access.
Once a user installs the malicious app, typically disguised as YouTube, WhatsApp, or local Russian apps like taxi or parking services, it requests permissions for SMS handling and Accessibility Services.
After approval, the malware disables Google Play Protect by simulating button taps, ensuring uninterrupted operation.
This expanded access enables ClayRat to perform a broad set of invasive actions. It can record keystrokes, capture PINs, passwords, and lock patterns, and automatically unlock the screen through its auto_unlock command.
The spyware also uses the MediaProjection API to continuously capture the screen and stream it to remote servers via WebSocket connections.
Overlays such as fake system updates or black screens conceal malicious activity, while custom “PIN overlays” collect sensitive data directly from victims.
The spyware’s distribution network remains aggressive and multifaceted.
Beyond phishing domains mimicking trusted platforms like YouTube Plus or Car Scanner ELM, researchers have found ClayRat samples hosted on Dropbox, showing that attackers are now exploiting legitimate cloud services to spread their payloads.
More than 700 unique APKs linked to the campaign have been identified, each using encrypted payloads and runtime decryption (via AES/CBC) to bypass Android’s security restrictions.
The updated malware version adds several new commands, including send_push_notification, which creates fake notifications designed to trick users into entering credentials that are immediately exfiltrated.
Other commands, such as start_desktop, enable full-screen streaming sessions similar to remote desktop control. At the same time, messages continue ClayRat’s signature propagation method, sending malicious links to every contact in the phone book.
Technical analysis shows that ClayRat communicates with its command‑and‑control servers using both HTTP and WebSocket protocols.
Data, including passwords, photos, SMS logs, and system information, is transmitted in encrypted form, reducing the likelihood of detection.
According to Zimperium, its Mobile Threat Defense and zDefend solutions detect and block all known ClayRat samples through on-device machine learning, without relying on cloud signatures.
The researchers warn that this campaign poses serious risks to enterprises using Bring Your Own Device (BYOD) models, as the spyware can intercept MFA codes, expose corporate credentials, and monitor confidential app screens.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
Exclusive Cyber Security News platform that provide in-depth analysis about Cyber Attacks, Malware infection, Data breaches, Vulnerabilities, New researches & other Cyber stories.
Contact Us: [email protected]
© Copyright 2024 – Cyber Press
Android Malware ClayRat Steals SMS Messages, Call Logs and Captures Photos – Cyber Press